Microsoft’s Digital Crimes Unit (DCU) has seized 240 fraudulent websites associated with an Egypt-based cybercrime facilitator. Abanoub Nady (known online as “MRxC0DER”) developed and sold “do it yourself” phish kits and fraudulently used the brand name “ONNX” to sell these services. Numerous cybercriminal and online threat actors purchased these kits and used them in widespread phishing campaigns to bypass additional security measures and break into Microsoft customer accounts. While all sectors are at risk, the financial services industry has been heavily targeted given the sensitive data and transactions they handle. In these instances, a successful phish can have devastating real-world consequences for the victims. It can result in the loss of significant amounts of money, including life savings, which, once stolen, can be very difficult to recover.
Phishing emails originating from these “do it yourself” kits make up a significant portion of the tens to hundreds of millions of phishing messages observed by Microsoft each month. The fraudulent ONNX operations are part of the broader “Phishing-as-a-Service” (PhaaS) industry and as noted in this year’s Microsoft Digital Defense Report, the operation was among the top five phish kit providers by email volume in the first half of 2024. Much like how e-commerce businesses sell products, Abanoub Nady and his associates marketed and sold their illicit offerings through branded storefronts, including the fraudulent “ONNX Store.” By targeting this prominent service, DCU is disrupting the illicit cybercriminal supply chain, thereby protecting customers from a variety of downstream threats, including financial fraud, data theft, and ransomware.
Targeting emerging cyber threats to protect users online
The fraudulent ONNX operation illustrates the advancing sophistication of online threats, including sophisticated “adversary-in-the-middle” (AiTM) phishing techniques. As organizations strengthen their cybersecurity measures, cybercriminals are evolving their tactics to evade them. AiTM phishing attacks – where attackers secretly inject themselves in network communications to steal credentials and cookies used to authenticate users’ identity – have become highly favored, if not the “go-to” method used by malicious actors to bypass the additional protections of Multifactor Authentication (MFA) defenses. As noted in this year’s Microsoft Digital Defense Report, Microsoft has observed a 146% rise in these AiTM attacks alone.
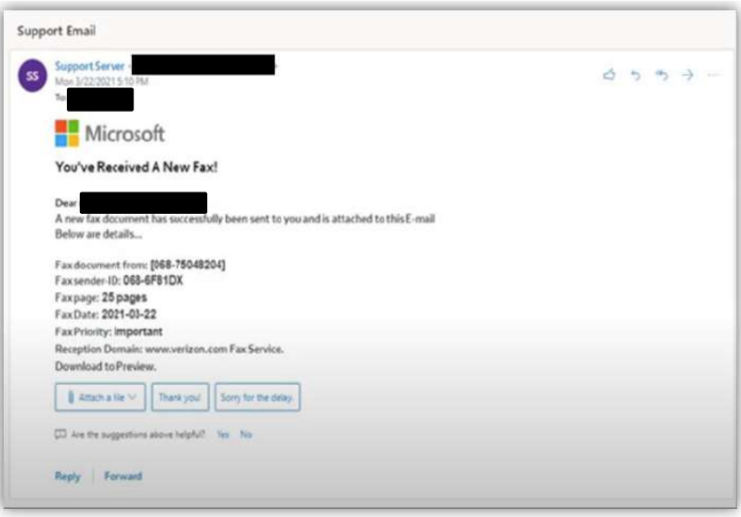
FINRA, the not-for-profit self-regulatory organization that oversees U.S. broker-dealers, recently issued a public Cyber Alert, warning of a spike in AiTM attacks against members fueled by the fraudulent ONNX operation. In this warning, FINRA highlighted new techniques employed by cybercriminals including QR code phishing (quishing) to bypass cybersecurity protections. “Quishing” uses embedded QR codes that, if scanned, direct online users to malicious impersonation domains — typically a fake sign-in page where users are prompted to enter credentials. Beginning around September 2023, Microsoft analysts observed a significant increase in phishing attempts using QR codes (to nearly one quarter of all email phishes). These attacks present a unique challenge for cybersecurity providers as they appear as an unreadable image.
Sending a strong message to cybercriminals
This action builds on the DCU’s strategy of disrupting the broader cybercriminal ecosystem and targeting the tools cybercriminals use to launch their attacks. Our goal in all cases is to protect customers by severing bad actors from the infrastructure required to operate and to deter future cybercriminal behavior by significantly raising the barriers of entry and the cost of doing business.
We are joined by co-plaintiff LF (Linux Foundation) Projects, LLC, the trademark owner of the actual registered “ONNX” name and logo. “ONNX” or Open Neural Network Exchange is an open standard format and open source runtime for representing machine learning models, enabling interoperability between different hardware, frameworks, and tools for easier deployment and scalability.
Together, we are taking affirmative action to protect online users globally rather than standing idly by while malicious actors illegally use our names and logos to enhance the perceived legitimacy of their attacks. In addition, and as DCU has in past actions where we independently identify an actor, we have chosen to publicly name a defendant – Abanoub Nady, who led the fraudulent ONNX operation – to serve as a further deterrent for cybercriminals and malicious actors online.
About the fraudulent ONNX criminal operation
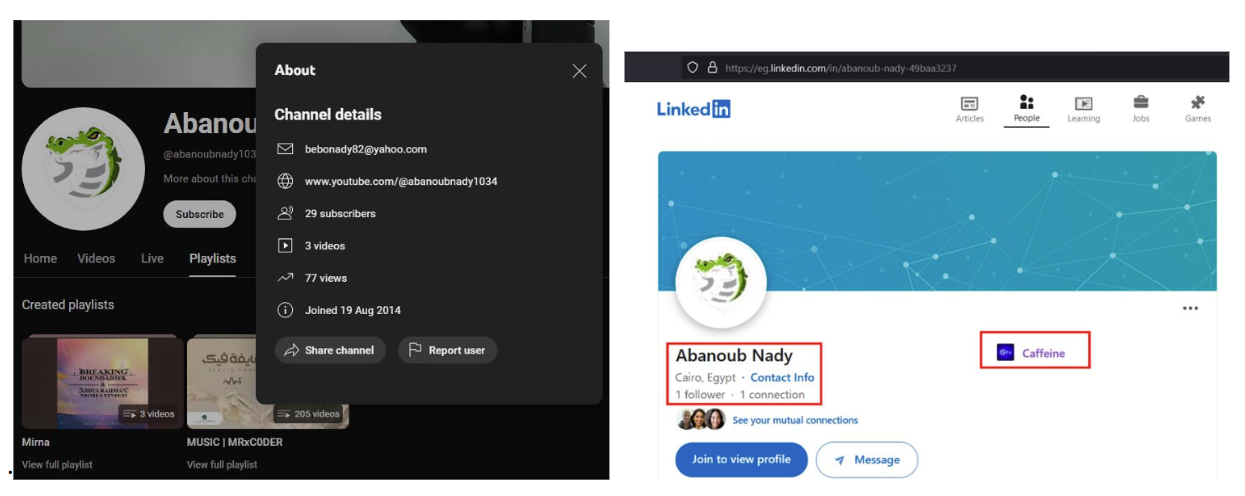
Many cybersecurity companies have looked into and published reports on the fraudulent ONNX operation, including DarkAtlas which Abanoub Nady earlier this year and EclecticIQ, which detailing how fraudulent ONNX operations were being used to target financial institutions. Microsoft has tracked activity tied to Abanoub Nady’s operation as far back as 2017. Nady fraudulently used the ONNX brand, but he also used other names in his operation, including “Caffeine” and more recently DCU observed Nady running the “FUHRER” operation. The phish kits are designed to send emails at scale, specifically for coordinated phishing campaigns. For instance, the fraudulent ONNX operation offers a subscription model, offering Basic, Professional, and Enterprise subscriptions, each for different tiers of access and support. Enterprise users can also purchase the add-on feature of “Unlimited VIP Support,” which is essentially ongoing technical support that provides step-by-step instructions on how to successfully use the phishing kits to commit cybercrime.

The phish kits are promoted, sold and configured almost exclusively through Telegram, as shown in the example below, which are paired with “how to” videos on social media platforms that provide guidance on the purchase and implementation of these phishing kits.
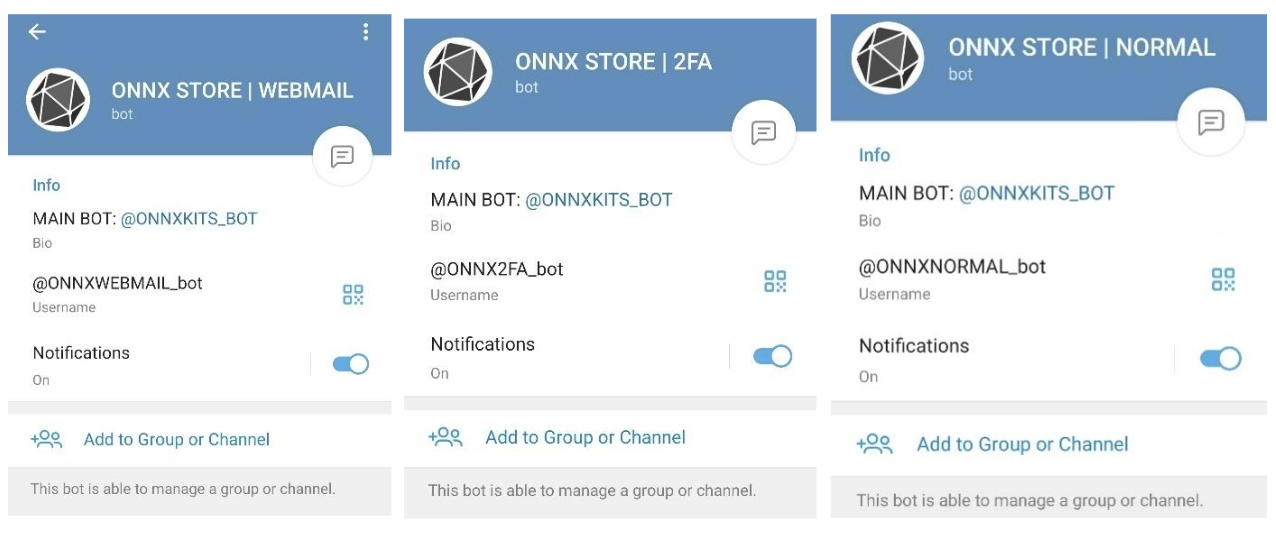
Once a kit is purchased, cybercriminal customers can conduct their own phishing attacks using the templates provided and the fraudulent ONNX technical infrastructure. They can use domains they purchase elsewhere and connect to the fraudulent ONNX technical infrastructure, enabling their phishing operations to grow and scale.
Through a civil court order unsealed today in the Eastern District of Virginia, this action redirects the malicious technical infrastructure to Microsoft, severing access of threat actors, including the fraudulent ONNX operation and its cybercrime customers, and permanently stopping the use of these domains in phishing attacks in the future.
Continuing our fight against the tools cybercriminals use in their attacks
As we’ve said before, no disruption is complete in one action. Effectively combatting cybercrime requires persistence and ongoing vigilance to disrupt new malicious infrastructure. While today’s legal action will substantially hamper the fraudulent ONNX’s operations, other providers will fill the void, and we expect threat actors will adapt their techniques in response. However, taking action sends a strong message to those who choose to replicate our services to harm users online: we will proactively pursue remedies to protect our services and our customers and are continuously improving our technical and legal strategies to have greater impact.
Furthermore, as cybercriminals continue to evolve their methods, it is crucial for organizations and individuals to stay informed and vigilant. By understanding the tactics employed by cybercriminals and implementing robust security measures, we can collectively work towards a safer digital environment. Continued collaboration, like the partnership with LF Projects, remains essential if we want to meaningfully dent the cyber threat landscape.
Microsoft’s DCU will continue to look for creative ways to protect people online and work with others across public and private sectors globally to meaningfully disrupt and deter cybercrime.
Nov. 11, 2024, 11:48a PT: Updated to include additional research on the fraudulent ONNX operations by other cybersecurity companies.